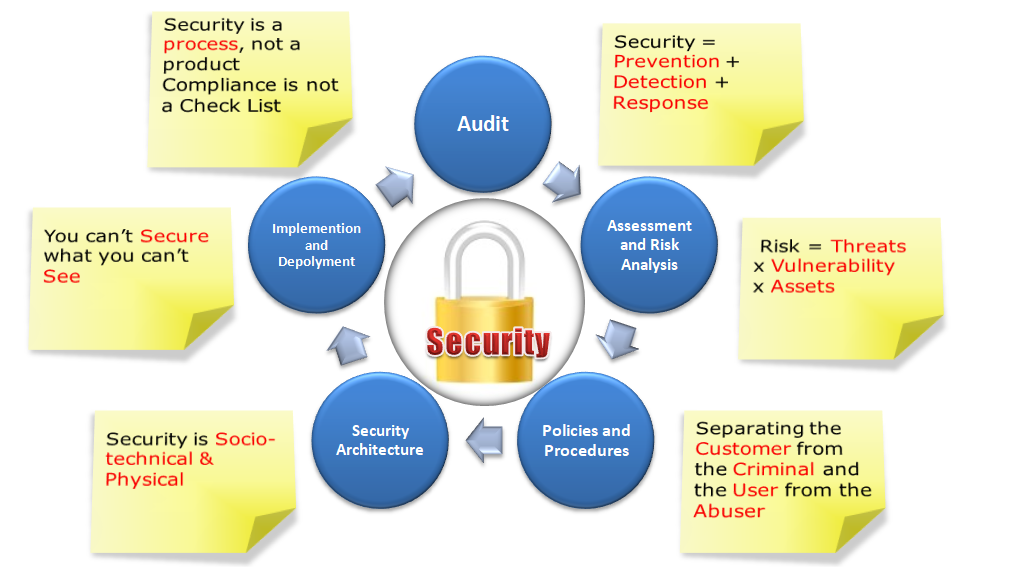
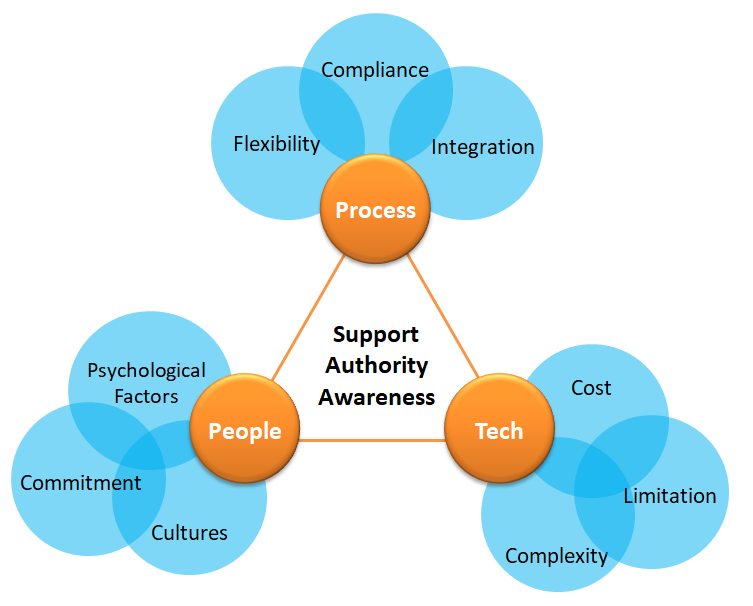
STME One Smart Solution
KINGDOM OF SAUDI ARABIA
Riyadh | Jeddah | Al Khobar
UNITED ARAB EMIRATES
Abu Dhabi |Dubai
BAHRAIN EGYPT KUWAIT
Manama | Cairo | Kuwait
JORDAN PAKISTAN UK
Amman | Karachi | London
QUICK LINKS
NEWS AND UPDATES
 STME Concludes Successful Participation in GITEX Technology Week 2018November 4, 2018 - 11:43 am
STME Concludes Successful Participation in GITEX Technology Week 2018November 4, 2018 - 11:43 am STME has been qualified by Saudi Exports to represent KSA in 38th GITEX Technology 2018September 20, 2018 - 12:32 pm
STME has been qualified by Saudi Exports to represent KSA in 38th GITEX Technology 2018September 20, 2018 - 12:32 pm
24/7 Support Service
We are all dedicated to serve you our best service, and satisfy your requirements all the way.
- KSA Support Line: 800 246 0006
- UAE Support Line: 800 8810
- Email: supportline@stme.com